Muvi - Secured Streaming Platform
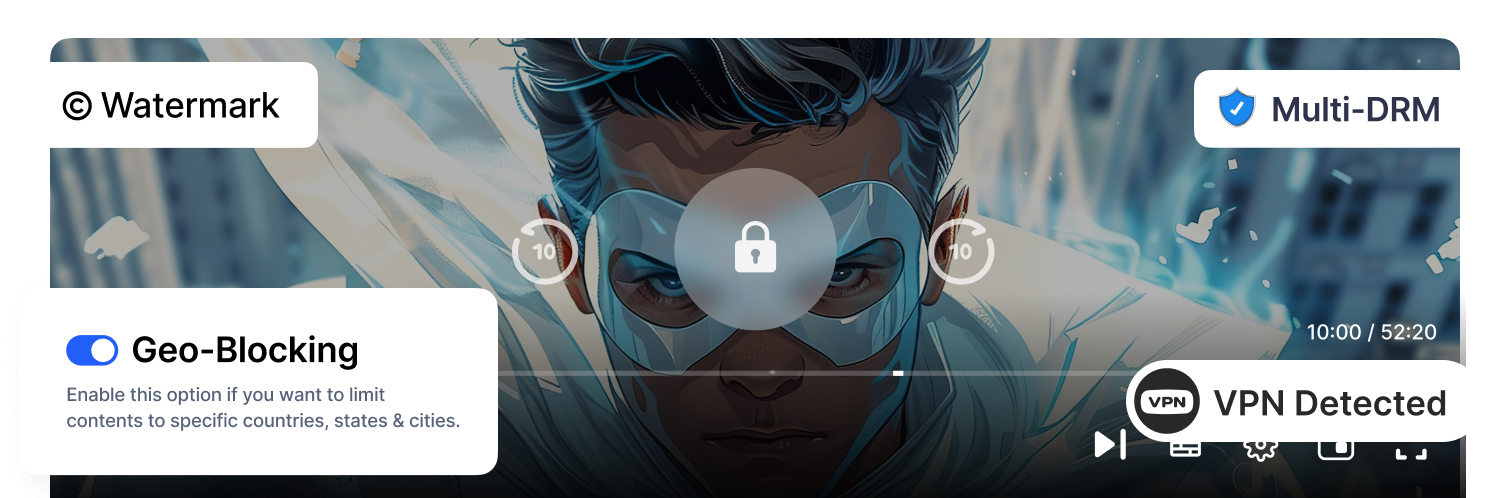
At Muvi, security isn’t an add-on — it’s built into the foundation of our OTT platform. Every asset, user, and stream is protected end-to-end with advanced safeguards. From upload to playback, content remains encrypted and shielded from piracy, breaches, and unauthorized access, ensuring your platform and viewers stay secure at all times.
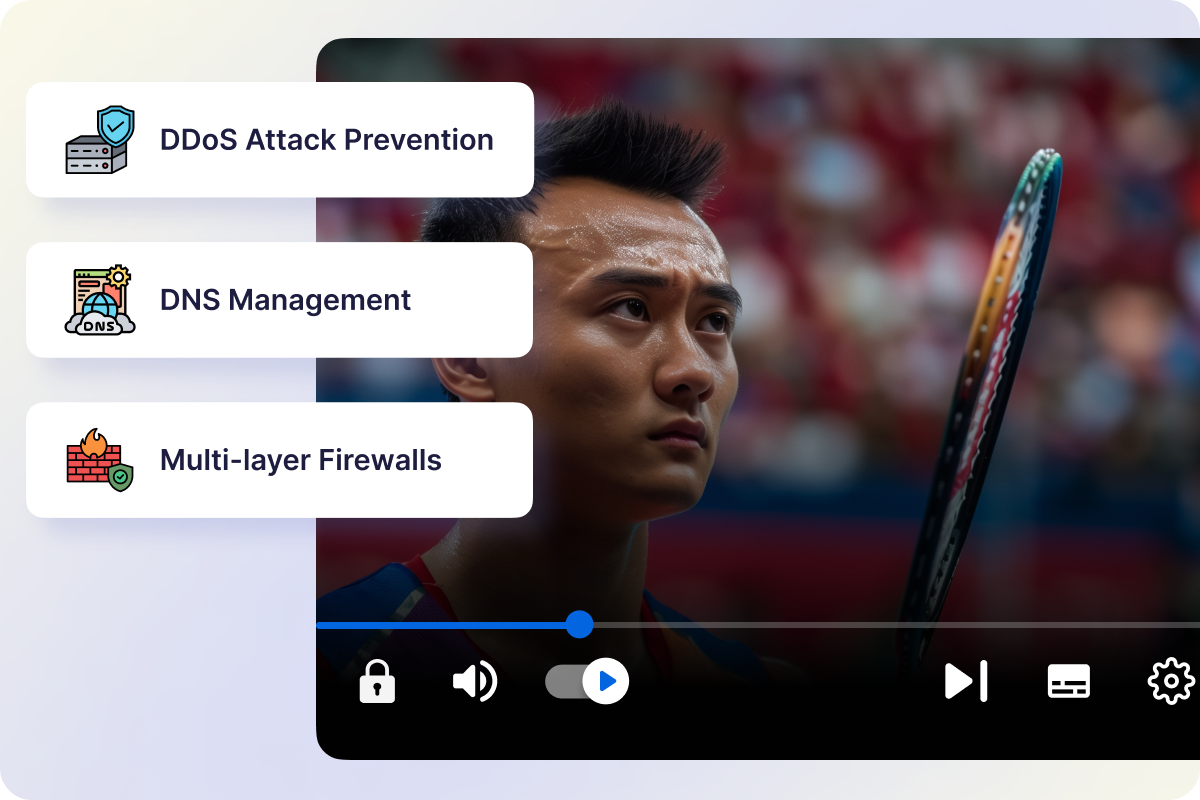
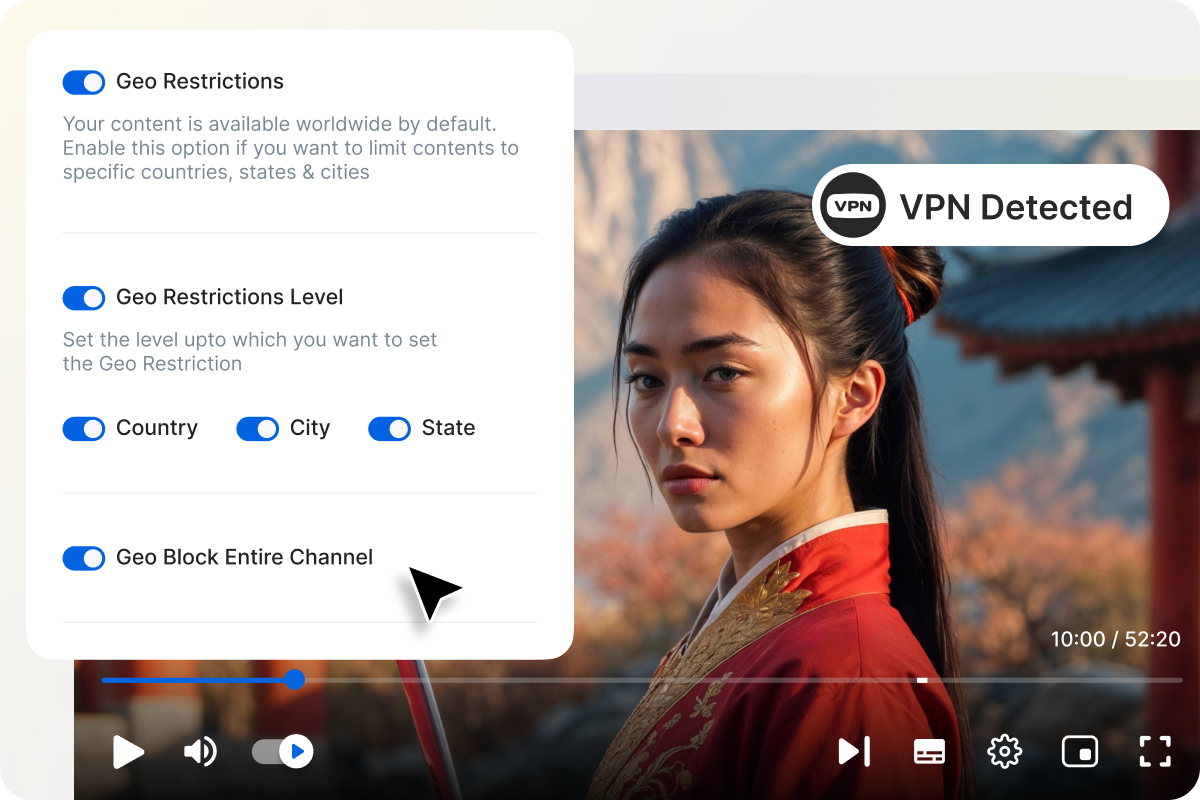
Server-Level Security & Multi-Layer Firewall
Muvi safeguards your data with enterprise-grade server protection, multi-layer firewalls, and 24×7 threat monitoring. Regular penetration tests, DDoS prevention, automated backups, and disaster recovery protocols ensure your platform stays secure and uninterrupted.
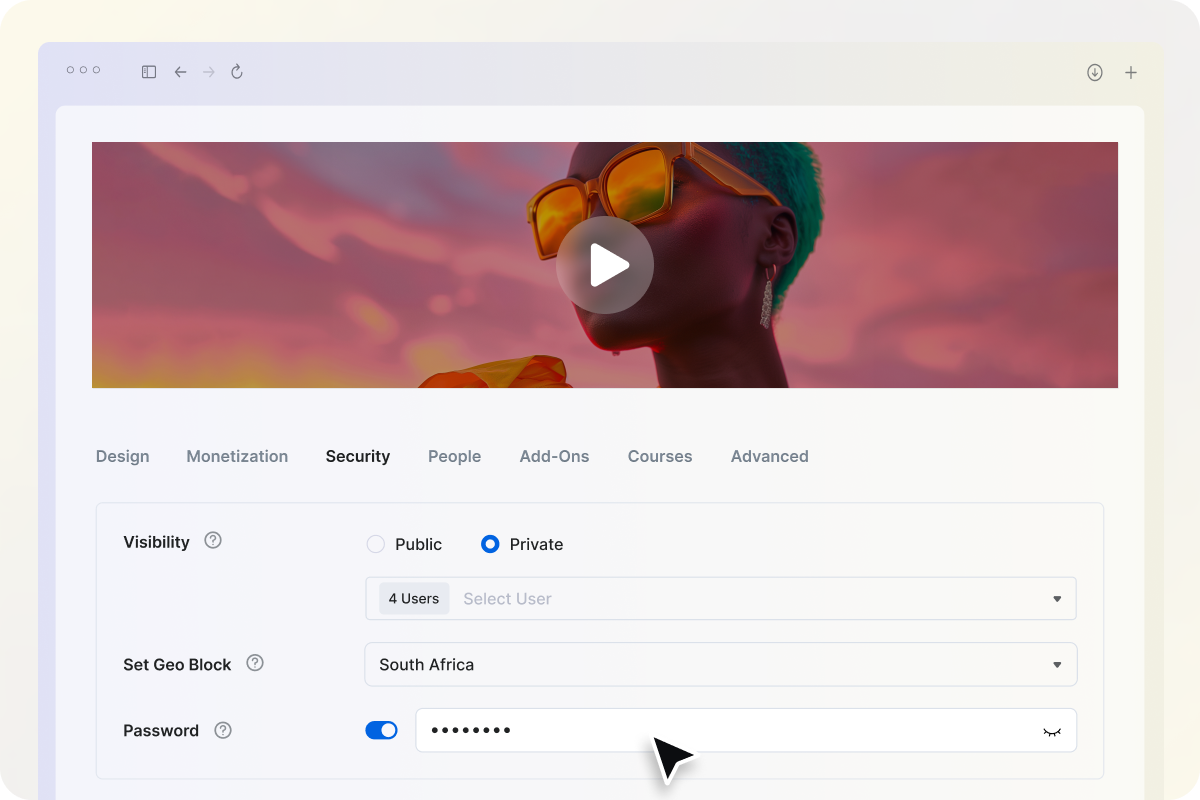
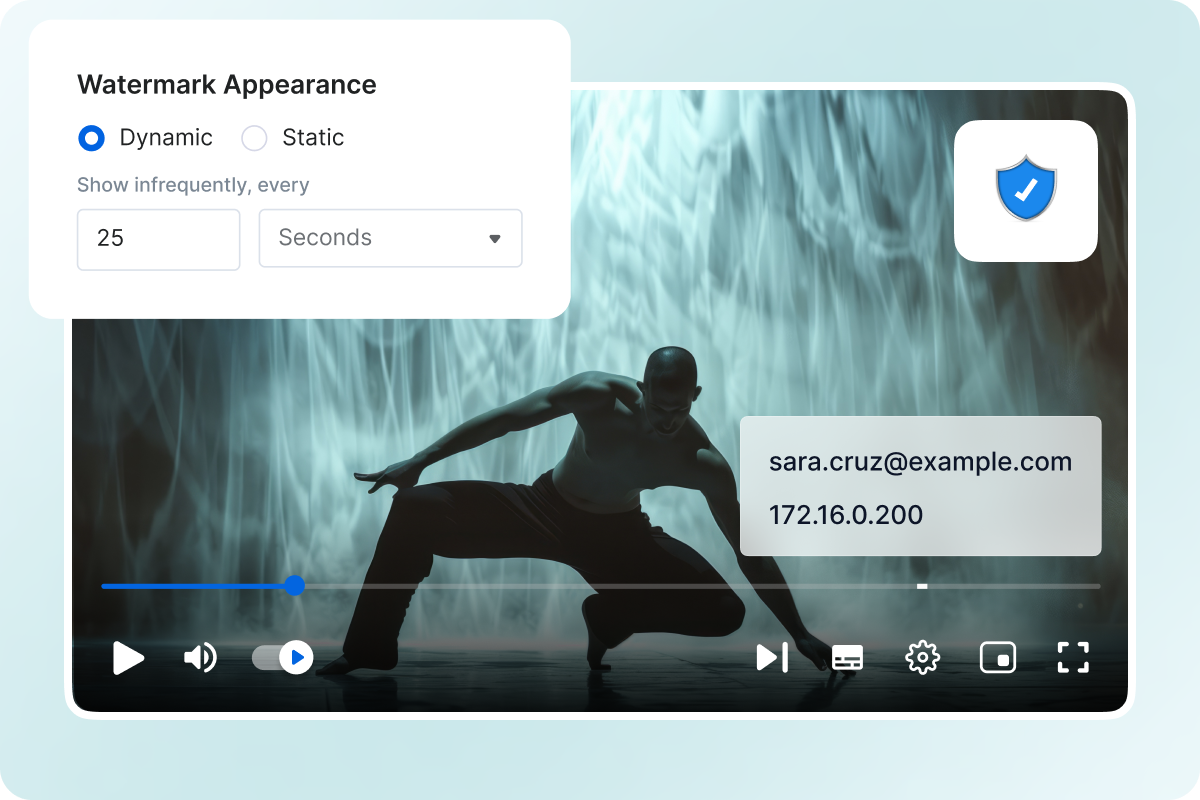
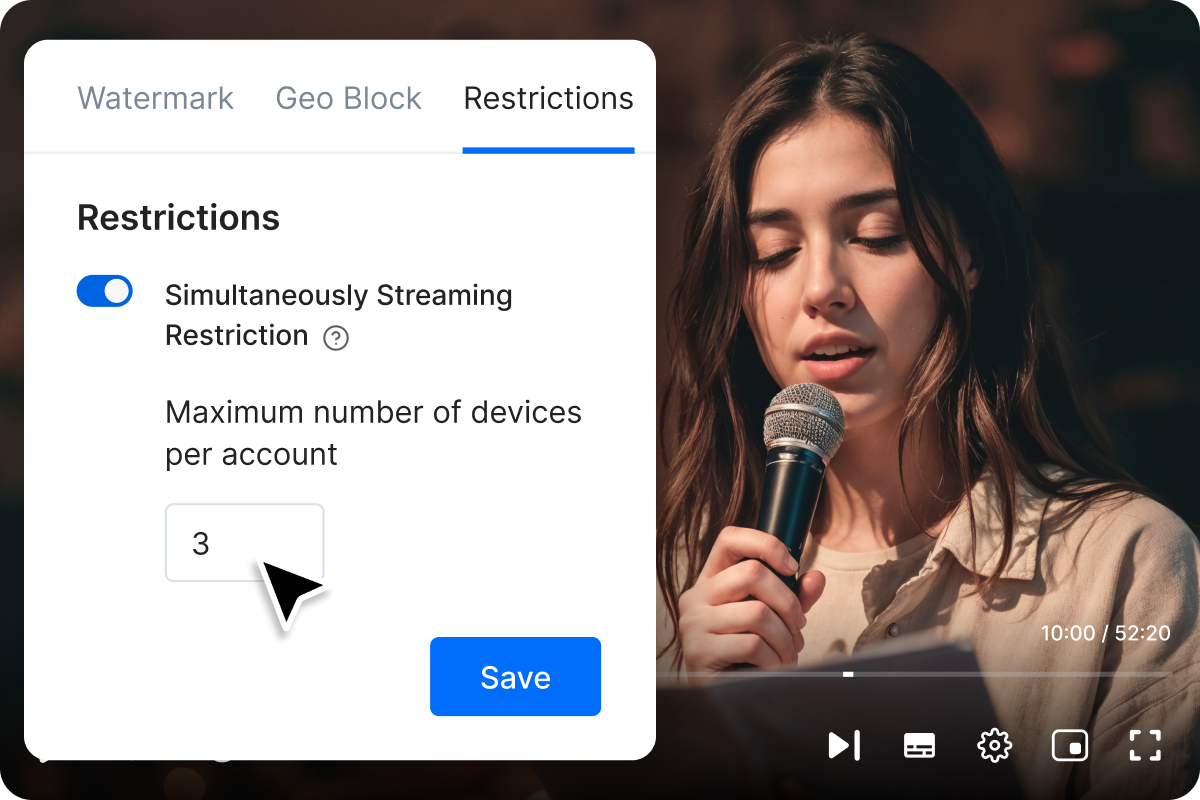
Password-Protected Content Sharing
Add password protection to your videos and live streams to prevent unauthorized access.
Only viewers with the correct password can unlock and play protected content, giving you total control over who watches what.
- Assign unique passwords to specific videos, live streams, or events.
- Restrict viewing to authorized audiences only.
- Strengthen content security alongside DRM, watermarking, and geo-blocking.

Start your 14 day free trial today
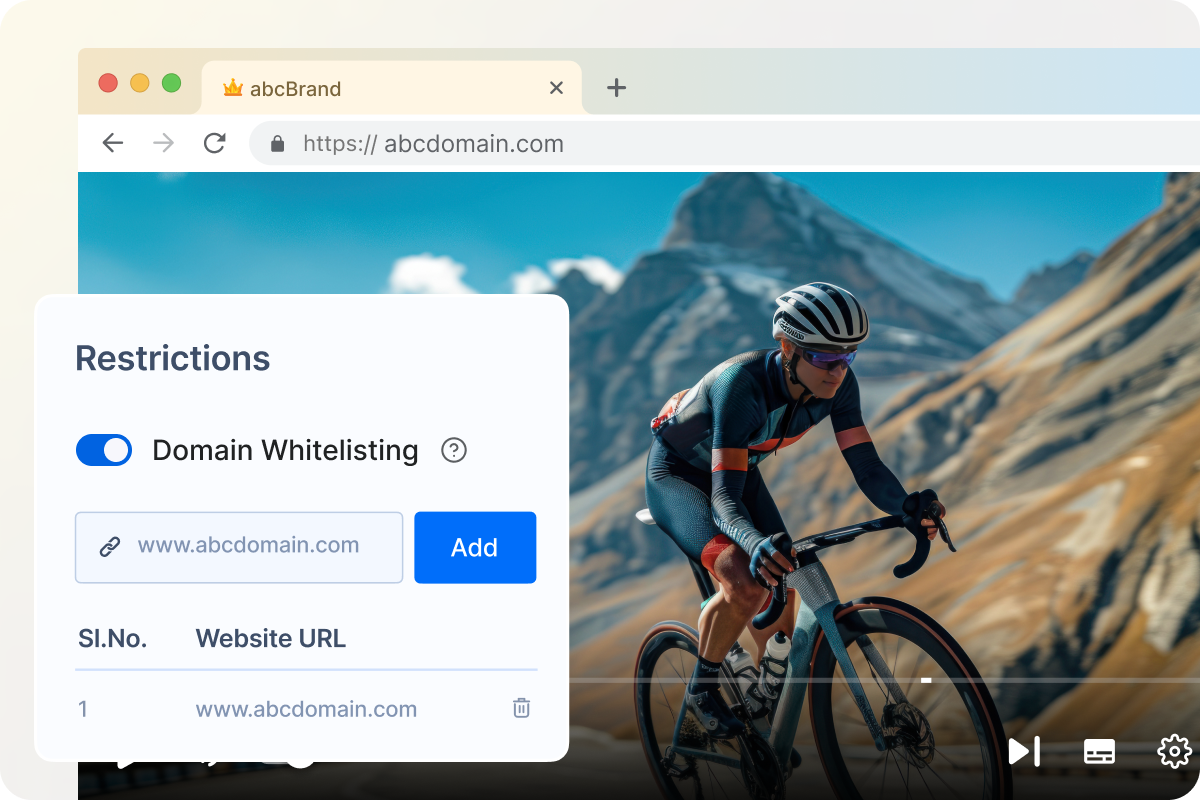
- White-listing for Embed Player
- Protection against illegal content usage & downloads
- ISO Certified Platform
Upgrade / Cancel Anytime. No Commitments.
Muvi will help with Data Migration, Customizations, and Integrations. Switch to Muvi today!
Migrate to MuviGet Your Free Trial Today. No Purchase Required
- Launch your very own Video/Audio Streaming Platform
- Get Websites and Apps across devices
- Stream Content across the Globe