Video piracy is a menace that is impacting streaming platforms worldwide. With emerging technologies, the pirates are becoming more and more skillful at their jobs, resulting in losses worth billions of dollars globally. If you are also facing piracy issues, deploying robust forensic watermarking techniques to protect your data can save you money.
Digital content is enormous and not just restricted to the entertainment industry. From education to defence to business communication, video finds a use case everywhere, and that is the reason digital content protection is a must to protect sensitive documents from misuse. While DRM’s are more than capable of restricting unauthorized streaming on devices, adding a forensic watermarking layer and visible watermarks acts as added security. This blog talks about forensic watermarking in detail and how you can implement robust watermarks it for a much safer video streaming business.
What is Forensic Watermarking or Digital Watermarking?
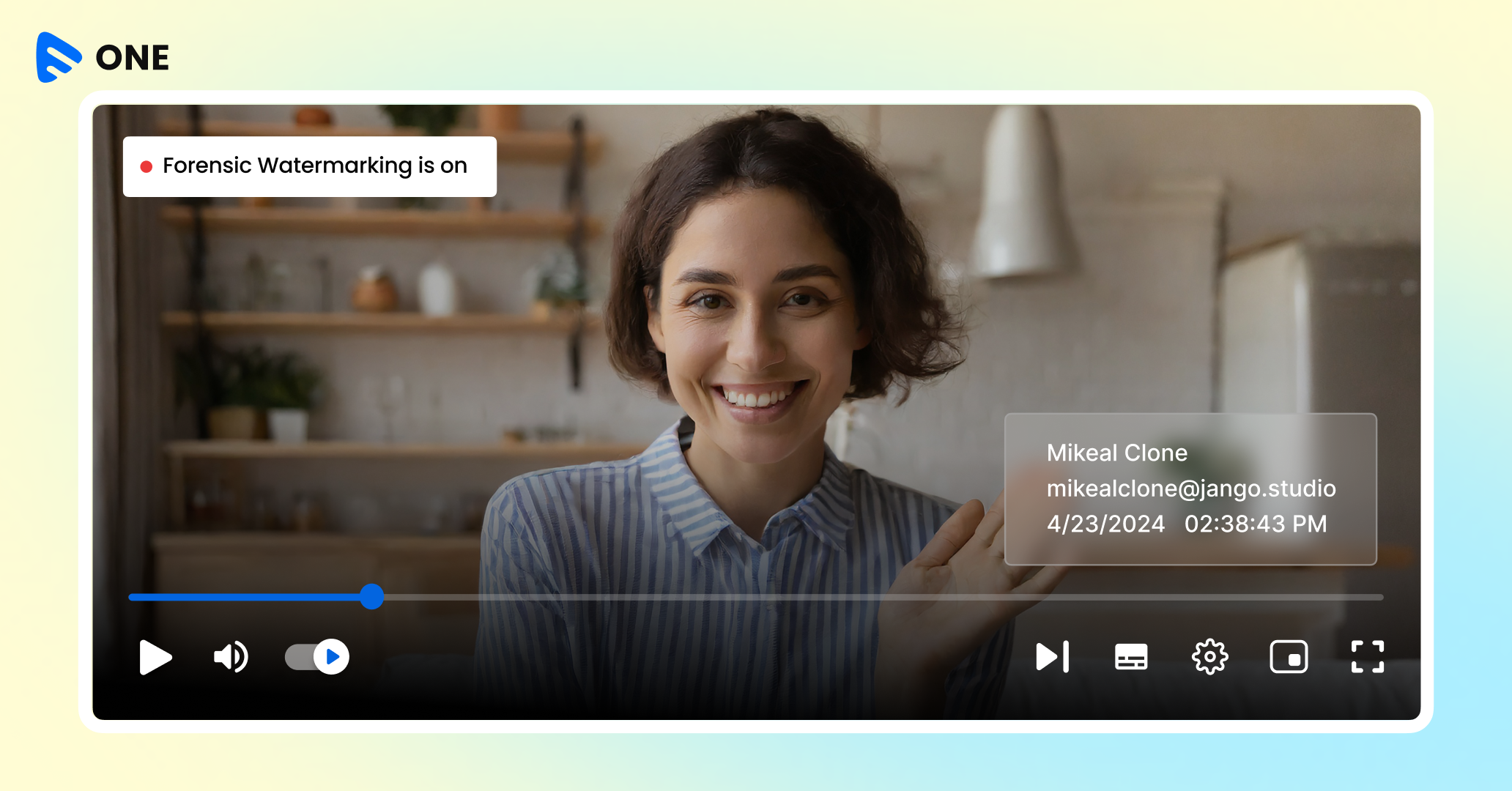
As the title suggests, it’s a silent digital guardian for your content. In simple words, it is a content protection technology that embeds invisible watermarks with traceable information into your video or audio files. In times of data leaks, this helps identify the source of the leak and take legal as well as corrective actions. Digital watermarking defines unique users, a particular stream, and help to track pirates and take action via digital watermarking algorithm.
Since these are embedded digitally, they are also known as digital watermarks and play a crucial role in digital content protection. Video watermarking has been around for a long time with visible watermarks, but with the advancements in data analytics and video technologies, forensic watermarking takes the digital assets protection game to the next level without hampering the end-user experience.
Difference Between Traditional and Digital Watermarking for Video Content
While you must have seen traditional visible watermarks where the logos of brands or some numeric codes are visible as part of the video, they do not serve the same purpose. Traditional watermarks are fragile watermarks and more commonly used for branding purposes, whereas forensic or digital watermarking is used for identification purposes.
Types of Forensic Watermarking
Forensic watermarking, or invisible watermarking, is an incredible technology that can be implemented in multiple ways depending on the use case. For instance, live streaming requires more of the Bitstream watermarks, whereas content that is multilingual and requires more than one distribution channel may need some sort of pre-embedding, or should we say offline watermarking.
Offline Watermarking
In this case, the watermarks are embedded before distribution to the initially sourced during the encoding process, and each video gets a unique identifier that can be applied for a particular distributor or channel for tamper detection. These are commonly used for transferring pre-release, VOD libraries transfer and distribution within studios. They are fairly easy to deploy but have scalability issues. In this case, sometimes visible watermarks are used.
Dynamic Watermarking
These watermarks are generated in real-time and embedded during the playback of the content. Each of these viewers or playback sessions, therefore, gets a unique watermark and can be traced should any leaks occur. These are scalable and can be used for OTT and live streaming requirements. They help prevent unauthorized use and watermarking videos enable better copyright protection. It even works for AI generated content.
Bitstream Watermarking
Bitstream watermarking, also known as compressed-domain watermarking, is a unique forensic watermarking technique where watermarks are directly embedded into the compressed video streams like H.264, HEVC or AV1. They are applied directly during compression. Videos do not have to be decoded and re-encoded again and again to digital watermarking. Owing to its efficiency, Bitstream watermarking is widely used in commercial streaming scenarios where timing and speed play a crucial role and video compression is required for quality.
A/B Variant Watermarking
As the name suggests, in A/B watermarking, the system creates two or more slightly different versions of a small content segment of digital watermarking with the slightest modification, and the video player then decides which version, A or B, C, and so on, has to be streamed to the user. In this way, no 2 users will receive the same pattern of watermarks, and greater the length of the video, the more unique versions of the watermarks can be created. This is a highly scalable method, but it has a video player dependency and, therefore, will have its own limitations in terms of security beyond the player environment. Therefore, they are mostly used for pre-screen releases, enterprise video training applications, and for internal sharing among post-production teams.
How Does Forensic Watermarking Work?
Now that we know the various types of watermarking, let’s understand how forensic watermarking works. Basically, there are 3 steps involved in forensic watermarking from generation to detection, but they are not limited to the process.
Step 1: Generating Watermarks
Watermarks are generated as per unique watermark codes that track the playback of original content data. This can be done primarily in 3 ways. They can be created for specific users, or as we call it session-based watermarking, where parameters such as IP address, user data like account number, timestamp, and session IDs are tracked for videos. There is also an option to embed device-based digital watermarking, where watermarks are generated based on the type of device a user is using. These imperceptible watermark codes are usually short binary or alphanumeric sequences.
Step 2: Embedding Digital Watermarking
The watermark is embedded into the video or audio signal using advanced algorithms.
There are two major ways to do this:
Pixel-domain embedding: Modifies the visual or audio signal itself (slight, imperceptible changes to brightness, color, or sound).
Bitstream embedding: Inserts the watermark into the compressed video file (in motion vectors, quantization parameters, etc.).
A/B watermark embedding, where unique sequences are created by altering very small elements of the video files or metadata.
Step 3: Content Streaming & Distribution
In most cases, every viewer, every session, and every distribution point receives a unique watermarked version of the content that is invisible to the naked eye and cannot be tracked, as they are mostly encrypted, and decryption happens at the platform owner’s side for enhanced security.
Whether the content is downloaded, live-streamed, or played via the internet, it is continuously monitored for any breach.
The next steps are simple. Whenever content appears illegally online, the content owner can simply capture or download the leaked video file and run it via watermark detection tools and match it with the internal records to find which user, stream, or partner leaked it. Further, legal actions as needed can be taken. The imperceptible watermarks makes the task much easier.
Why is Forensic Watermarking Necessary?
Digital watermarking is an essential component of digital forensics, and if used properly, it can help content owners save millions of dollars by early detection and timely action. Other video protection tools, such as DRMs, are required to protect and prevent leakage, but should leakage occur, it is these video watermarks that help catch the culprits and minimize losses. Here are a few reasons why forensic watermarking should be an integral part of your content security protocols.
Forensic watermark provides a robust capability to identify the source. So the source can be held accountable and paid content can be protected.
Since they are literally invisible, it does not hinder the experience of an end user. They lie hidden in meta data and is invisible to the human eye across images or videos.
As part of anti-piracy solutions, it is highly useful for content where potential revenue loss from piracy outweighs the feature’s pricing.
Forensic watermarking coupled with DRM, although not foolproof, can improve chances of mitigating piracy concerns in both preventive and reactive ways. Using digital watermarking, you protect quality content right from upload, define its ownership and help prevent brand erosion.
Secured Streaming with Muvi One Digital Content Protection
At Muvi, we understand the efforts and hard work that you put in while setting up and launching your OTT streaming solution. Therefore, as part of our robust content protection measures, which include multi-level DRMs, access controls, and AWS-enabled content protection, we also deploy forensic watermarking or digital watermarking at your request.
Content delivery is a crucial process, and in spite of all protection measures deployed, leaks can occur. Should they occur, you must be ready to track leaks and take timely action. Forensic watermarks are an essential component of digital forensics and must be used to restrict video piracy attempts.
Take a free 14-day trial to learn more about how Muvi One can make your content secure at every step of the process.







Add your comment