Amazon CloudFront is a leading global content delivery network (CDN) from Amazon Web Services (AWS) renowned for delivering applications, videos, websites and APIs to viewers across the globe at lightning fast speed.
Amazon S3 is one of the most used AWS architectures that is used as the origin to host content and CloudFront, which is used to deliver them to viewers. When using this architecture, customers can leverage CloudFront’s origin access identity (OAI) to secure S3 bucket access to CloudFront only. However, recently, AWS has introduced a new function named OAC that replaces OAI with some brand new features.
1.What is OAC?
AWS recently announced the new Origin Access Control (OAC) feature for CloudFront. This is a successor of the Origin Access Identity (OAI).As per our architecture we are using Amazon S3 as the origin to host content like websites and videos, and use CloudFront to deliver them to viewers. Now we are using CloudFront’s origin access identity (OAI) to secure S3 origin access to CloudFront only.
2.How is it more secure than OAI?
While OAI provides a secure way to access S3 origins to CloudFront, it has limitations such as not supporting granular policy configurations, HTTP and HTTPS requests that use the POST method in AWS regions that require AWS Signature Version 4 (SigV4), or integrating with SSE-KMS. In larger workflows, where S3 is also linked with other AWS services like amazon s3 to rds, these limitations can become more apparent, making OAC a more future-proof solution. To strengthen security and deepen feature integrations, AWS has introduced origin access control (OAC), a new feature that secures S3 origins by permitting access to the designated distributions only. OAC is based on an AWS best practice of using IAM service principals to authenticate with S3 origins.
Compared with OAI, some of the notable enhancements OAC provides include:
- OAC is implemented with enhanced security practices like short term credentials, frequent credential rotations, and resource-based policies. They strengthen your distributions’ security posture and provide better protections against attacks like confused deputy.
- Comprehensive HTTP methods support- OAC supports GET, PUT, POST, PATCH, DELETE, OPTIONS, and HEAD.
- SSE-KMS – OAC supports downloading and uploading S3 objects encrypted with SSE-KMS.
- Access S3 in all AWS regions – OAC supports accessing S3 in all AWS regions, including existing regions and all future regions. In contrast, OAI will only be supported in existing AWS regions and regions launched before December 2022.
If you’re preparing for AWS certifications, utilizing Amazon AWS Exam Dumps can provide additional insights into these features and security enhancements.
3. How can we create/enable this feature?
- Sign in to the AWS Management Console and open the CloudFront console.
- Choose Create Distribution.
- In the Origin configuration section, select an S3 origin from the Origin domain drop-down list.
- You can optionally configure an origin path to append to the origin domain name for origin requests.
- Enter a name to uniquely identify the current origin configuration.
- Choose Origin access control settings.
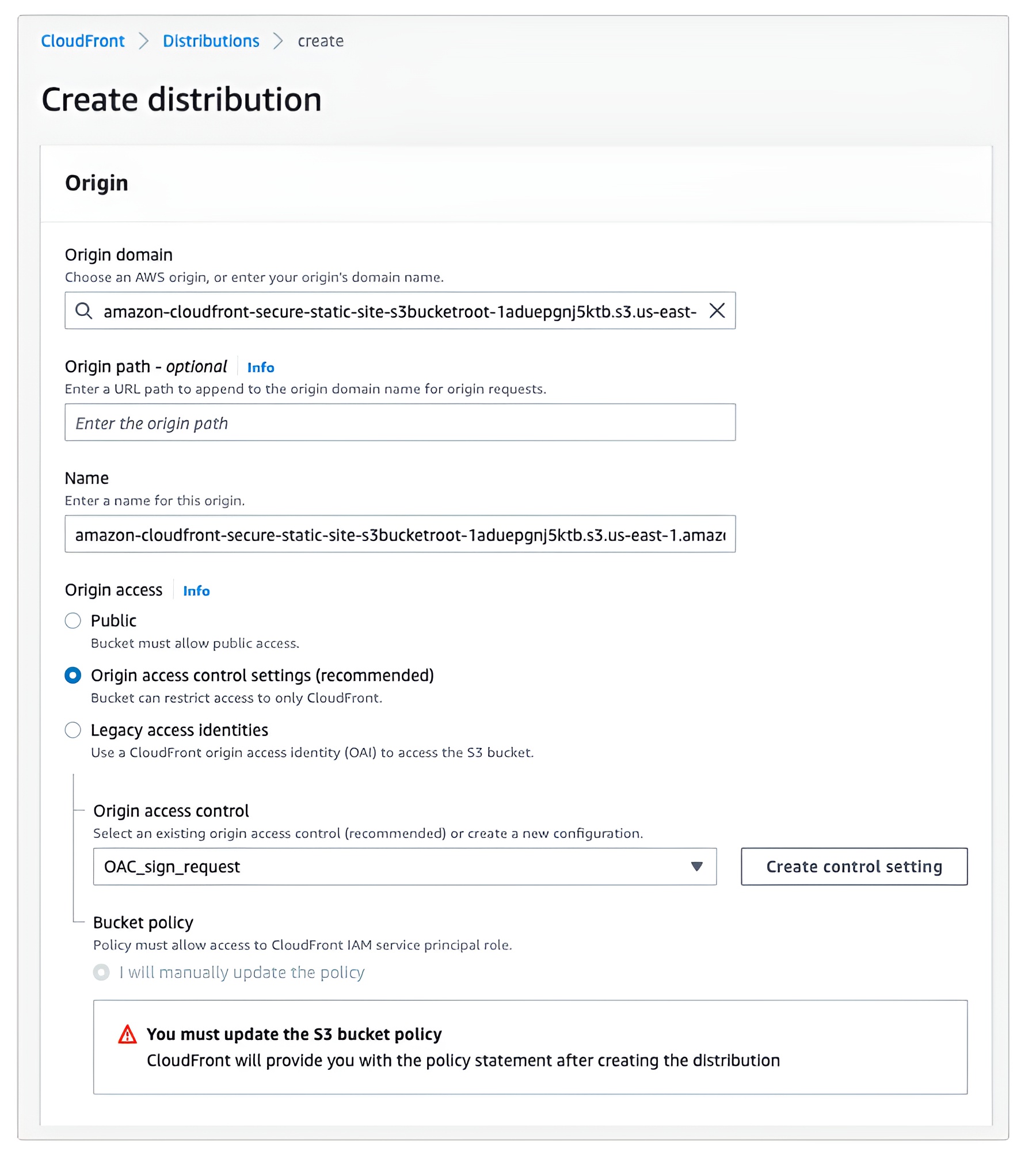
7. You can choose an existing origin access control or create a new control setting with one of three signing options.
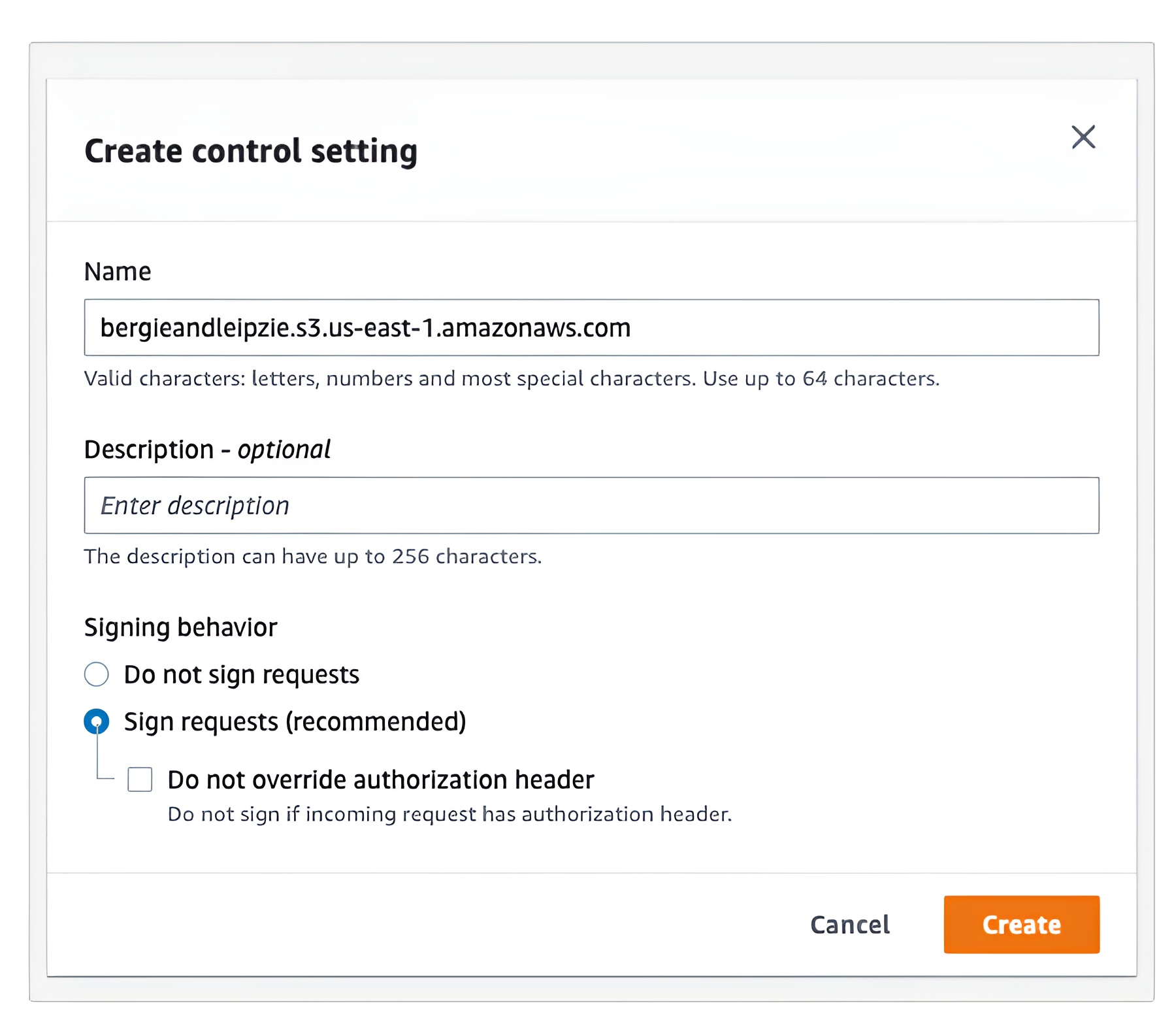
- Follow the detailed instructions here on how to configure the rest of the settings
- Select ‘Create distribution’ at the bottom of the page once all the configuration settings have been chosen
- Once the distribution is successfully created, you must update the S3 bucket policy, you can reference the policy statement provided on distribution detail page (Figure 3)
- Note that the policy provided only includes permissions to read objects from S3. If you would like to also upload objects to S3, you must update the policy with additional permissions for “s3:PutObject”.
4.How can we configure OAC when updating an existing CloudFront distribution ?
- Sign in to the AWS Management Console and open the CloudFront console.
- Select one of the distributions from the list
- Select the Origins tab and choose the S3 origin which you want to associate with an origin access control setting
- If the origin is not using any access mechanism, it will show as public. If the origin is already using OAI, it will show as “Legacy access identifies”. To use OAC, select “Origin access control settings” and choose an existing origin access control or create a new control setting with one of three signing options.
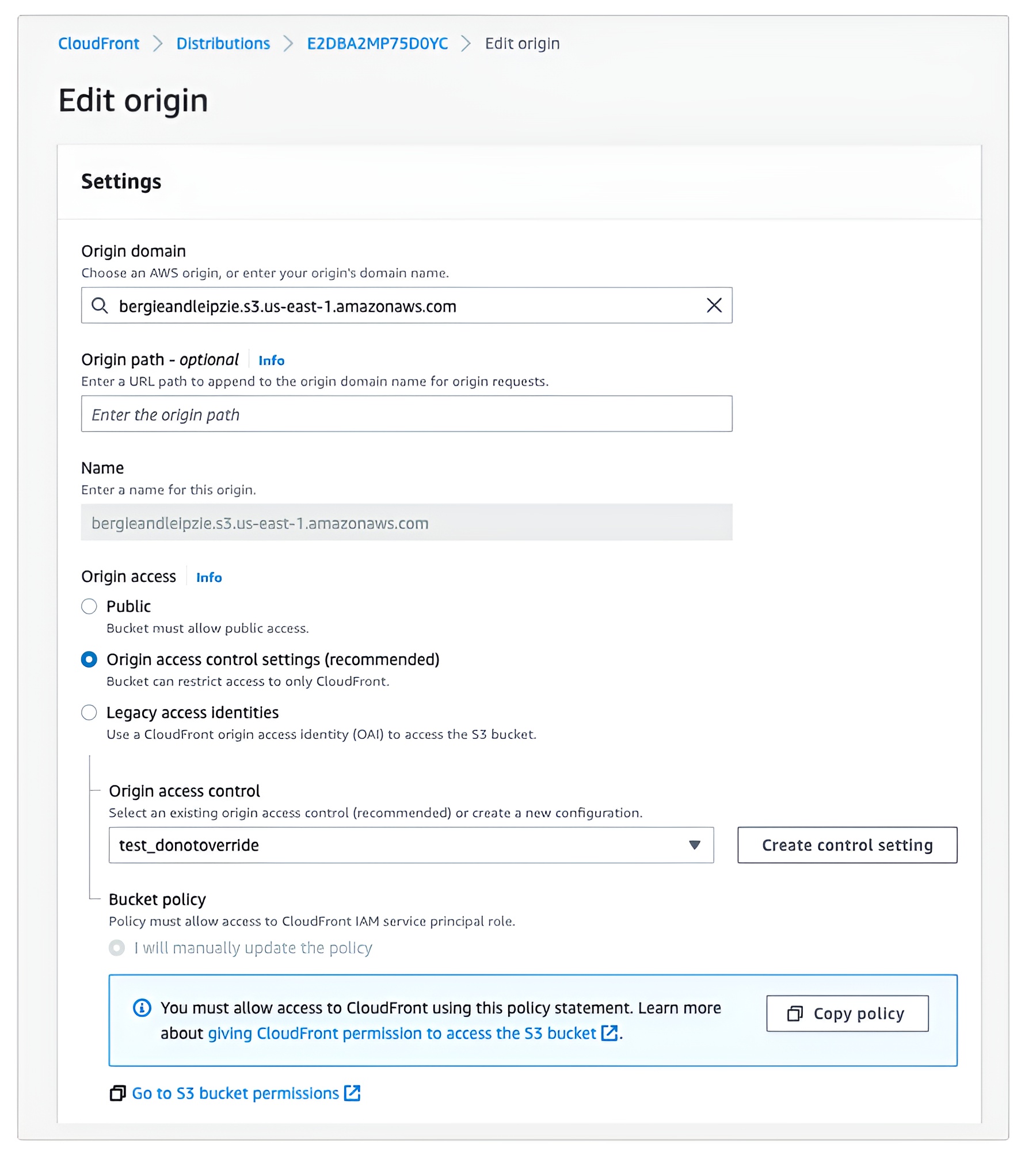
5. You must update the S3 policy to allow CloudFront IAM service principal and your distribution resource to access the S3 bucket. Unlike configuring origin access when creating distribution where you can update the policy only after the distribution is created, when updating a distribution, you can, and we indeed recommend, that you update the policy to allow access to both OAI and OAC, prior to saving the origin configuration, to reduce the service downtime to zero. The following is a sample policy that allows access to both OAI and OAC.
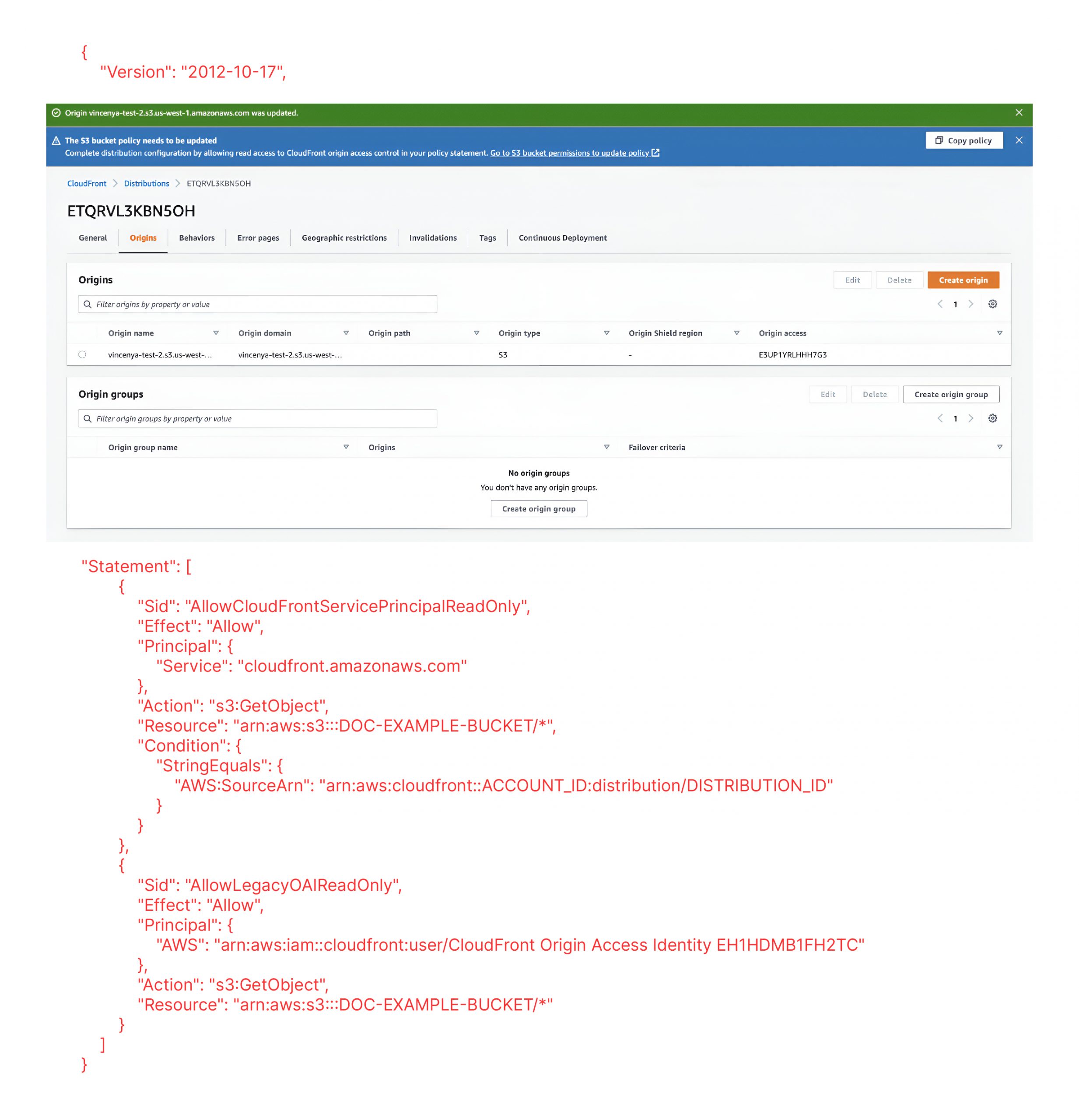
6. Similar to configure OAC when creating a distribution, the policy CloudFront provided only includes permissions to read objects from S3. If you would like to also upload objects to S3, you must update the policy with additional permissions for “s3:PutObject”
7. At the bottom of the page, choose Save
5. How can we Enable SSE-KMS for CloudFront OAC ?
AWS Well-Architected recommends protecting our data in transit and at rest. If we are using OAI, your data is already protected in transit, and we can protect our data at rest using Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3).
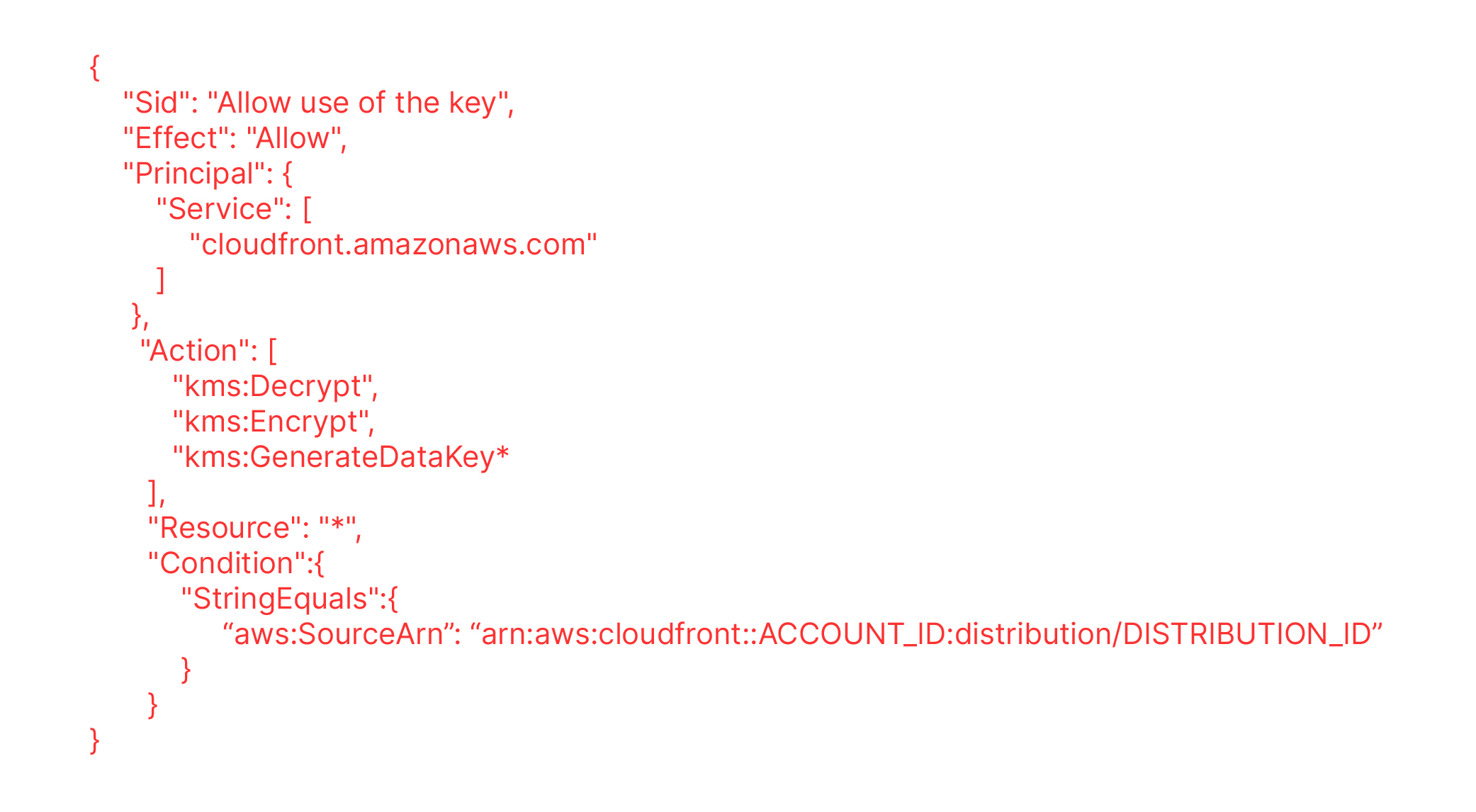
We need to configure your KMS policy to allow CloudFront IAM service principal to access our KMS keys. Adding aws:SourceArn condition key allows only a specific CloudFront distribution to access SSE-KMS encrypted objects using this key policy.
- Open the KMS console.
- Select the customer managed KMS key that is used to encrypt the content in the S3 origin
- Select the Key policy tab
4. Update the KMS key policy to give access to CloudFront Service Principle
6.Do I need to migrate to OAC?
To answer this question CloudFront supports both the new OAC and legacy OAI. AWS recommends using OAC for its latest security best practices and additional functionalities. One limitation of OAI over OAC will be, OAI will only be supported in existing AWS regions and regions launched before December 2022 but CloudFront Origin Access Control is now available worldwide except for AWS China regions.
Wrapping Up,
AWS CloudFront origin access control is now available globally. In this blog, I have tried to explain what OAC is and how it is different from OAI in the AWS management console itself. Although OAI provides ample security, OAC is recommended for enhanced security as it secures S3 origins by permitting access to the designated distributions only.
This blog has been written by Abinash Bhutia












Add your comment