SSO or Single Sign On is an advanced user-login technology where the user needs to put their login credentials on only one screen, but they gain access to multiple applications and sessions. It works by combining several login screens into one single screen, and hence the user needs to enter their login credentials on only one screen.
Though it seems very simple, technically, it is an extremely complicated process, with multiple benefits. In this blog, we will explain the technology behind SSO in detail, understand how SSO works, why SSO is important for security, and how it can benefit both businesses and users. So, let’s get started!
What is Single Sign On (SSO)?
SSO stands for “Single Sign On”. It is often used by businesses or IT teams that manage multiple SaaS applications. The main motive for implementing this technology is to ease the login process for users without compromising on security.
The technology is based on a very simple logic of one-time authentication and multiple access. Let’s understand it using an example. Suppose you visit a restaurant regularly. But every time you need to show your ID card and go through the authentication process, that takes a lot of time. Also, you need to go through the same process whenever you visit any other restaurant of the same restaurant chain. This process is hectic not only for you but for the restaurant admins as well!
So, to simplify the process, the restaurant admins can grant you an access pass once, after authenticating your identity. Whenever you visit any restaurant run by the same chain next time, you just need to show that already authenticated pass, and you are allowed to enter without further authentication. This process simplifies work for both users and admins.
Implementation of a similar process in the digital world can be done using SSO. In the Single Sign On technology, the users who log in to any app are asked to enter their login credentials only once. Thereafter, they can access multiple SaaS platforms, applications, and services related to the mother app where they logged in before. They don’t need to enter their login credentials again and again.
How does SSO Work?
Whenever you try to log in to any application, the app first authenticates you before granting access. When SSO technology is implemented, it authenticates the user, who is trying to log in, for all the applications the user has been given rights to, at a single authentication session. Hence, it eliminates further login prompts if the user switches applications till the original session has not expired.
There are many ways to implement SSO, IP Networks using cookies being the easiest one amongst them. But, we will also cover the more complex ones in this blog later on.
Any SSO system depends on two major components:
- Identity Providers (IP): Identity providers are statements that read the authentication, authorization, and attributes related to principals. After reading, they generate assertions.
- Service Providers: They depend on the assertions issued by the IPs.
The entire process of Sign Sign On depends on this assertion-based connection between identity providers and service providers.
Architectural Diagram of SSO
The Single Sign On (SSO) technology can be represented using the technical diagram given below:
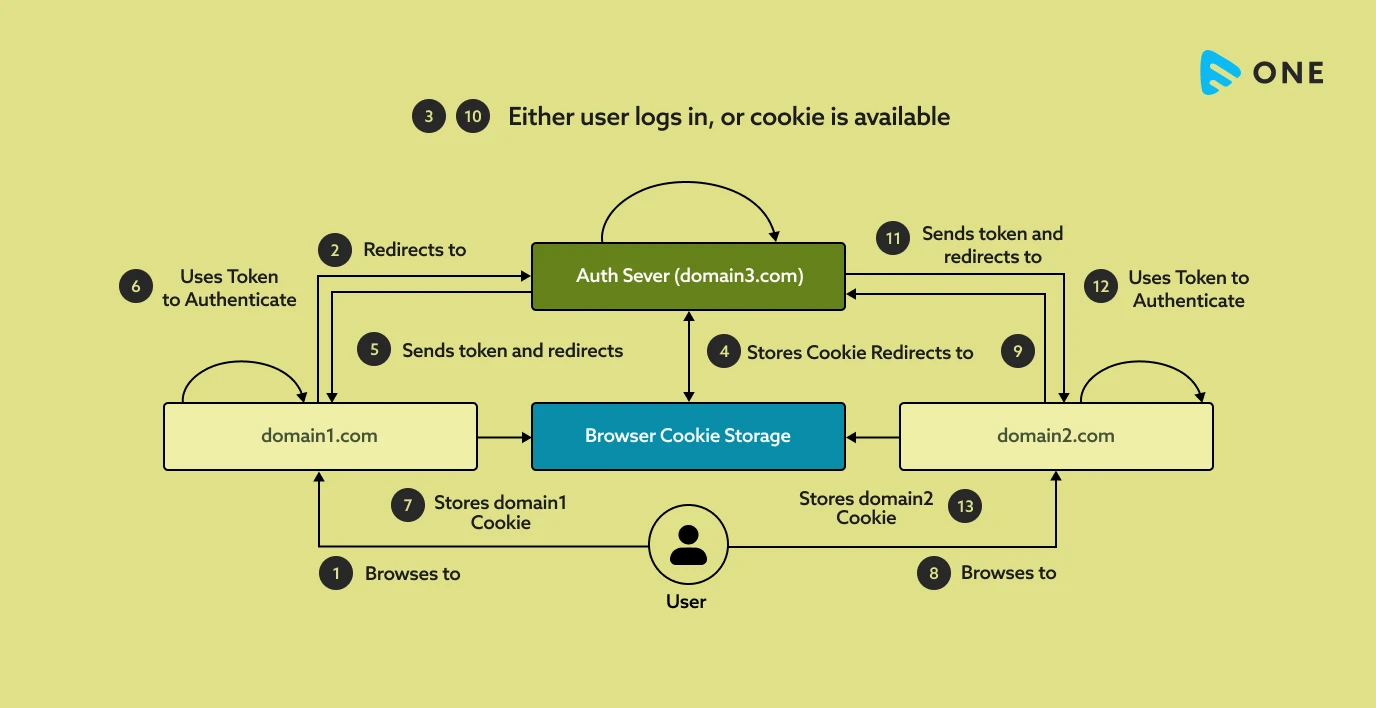
Before SSO vs After SSO
Now you might be thinking, what difference can be made by implementing Single Sign On (SSO)? Before SSO, the user needs to fill in their login credentials into multiple different windows and sessions, to gain access to different apps and platforms. However, after SSO, the user will insert login credentials only one single time but will be able to access multiple platforms.
Different Ways of Implementing SSO
Some of the ways of implementing SSO are as follows:
- SAML 2.0 Web SSO: SAML stands for “Security Assertion Markup Language”. It is an XML-based data exchange format. It is used for exchanging authentication and authorization data between an IP and a SP. It is often used for single sign on (SSO) in web browsers.
- OAuth2-OpenID Connect: OpenID Connect is an identity layer on top of the OAuth 2.0 protocol. It allows admins to verify the identity of an end user. The authentication is performed by an IP.
Apart from these, OpenID, WS-Trust, WS-Federation, and Integrated Windows Authentication are some of the other ways of implementing SSO. In this blog, we will take a detailed look at how OAuth 2.0 and OpenID Connect can be used to implement SSO. So, let’s begin.
SSO Integration and Enabling – SSO Technologies Explained
As discussed above, OpenID is built on top of OAuth 2.0. So, to understand Open ID, you will have to first understand what is OAuth and OAuth 2.0.
What is OAuth and OAuth 2.0?
OAuth is an open standard for access delegation. Using OAuth, internet users can grant access to their information, which they already have given to your website, to some third-party websites or applications, without giving away the passwords.
Many big tech companies, like Amazon, Google, Facebook, Microsoft, etc use this technology to allow their users to share their account information with third-party applications and websites. This is precisely the tech that is in play while you try to log in to any website or platform using your “Google” or “Facebook” accounts.
OAuth 2.0 is an upgraded version of the OAuth framework. It was published as RFC 6749, and the Bearer Token Usage as RFC 6750. Both these standards track Requests for Comments. They were launched in October 2012. Currently, OAuth 2.0 is the industry-standard protocol for authorization.
What is OpenID Connect?
As explained before, OpenID Connect helps the admins to verify the identity of the end users, using OAuth 2.0 protocol. This verification is achieved based on the verification performed by the authorization server. Here, this authorization server actually acts like an Identity Provider or IP.
Alongside verifying the identity, the admins can also obtain basic profile information about the end user in an interoperable and REST-like manner. This process specifies a RESTful HTTP API, using JSON as a data format. This technology can be used on and off the web.
The end goal of OpenID Connect is to allow the end users to log in and access content from multiple websites and platforms via a single sign-in session.
What is OP?
OP is the OpenID Connect Provider. It provides authentication services using the OpenID standard. The authentication is provided in the form of an ID Token, to the web application or RP, which we will discuss next.
This ID Token contains a JSON document, which passes statements (basically information and data) to the RP on when and how the user was authenticated. Along with that, it also passes on instructions on the time period for which the user session can be trusted.
What is RP?
If OP is the information sender, then RP is the receiver. Now after receiving the information, it will have to reply and act upon it. So, in most simple words, RP is nothing but “Replying Party”. It has two jobs:
- First, it seeks the necessary authentication-related information from the OP, by making service requests to the OP.
- After the authentication process (which is carried out by OP), RP receives the information from the OP and authenticates the users accordingly.
Let’s now understand how to manage sessions using OpenID.
How to Manage Sessions Using OpenID?
Managing sessions using OpenID is extremely simple. Because the admins have nothing to do much here. During the authentication, the JSON file that OP sends to RP already contains the details of the login time of the user, and for how long this session can be trusted.
Both these values remain opaque to the RP. So, the RP just keeps track of the session and sends a reply back to the OP in its postMessage calls from the RP iframe to the OP. This reply is sent so that the OP can correlate to it.
Single Logout or Global Logout (SLO)
Any login session cannot be forever. So just like single sign-on or SSO, there is a Single Logout or SLO, which is equally important. SLO, also called Global Logout, is possible when your OP supports the session management by OpenID.
This OpenID Connect Session Management offers a specific window to RP via which it can monitor the login status of a user. Whenever a user logs out of the OP, all the RPs where the user had logged in automatically log out the users from the respective sessions.
How Does SSO Authentication Works? – Authentication Grant for OAuth 2.0
Now that we have covered the basic technique behind Single Sign On, it’s time to deep dive into the authentication process, which is the backbone of SSO.
If you are using OAuth 2.0 protocol, then the authentication will take place through the Authentication Grant. There are basically, two types of Authentication Grant in OAuth 2.0:
- Implicit Grant
- Authorization-code Grant
Let’s take a look at both of them one by one.
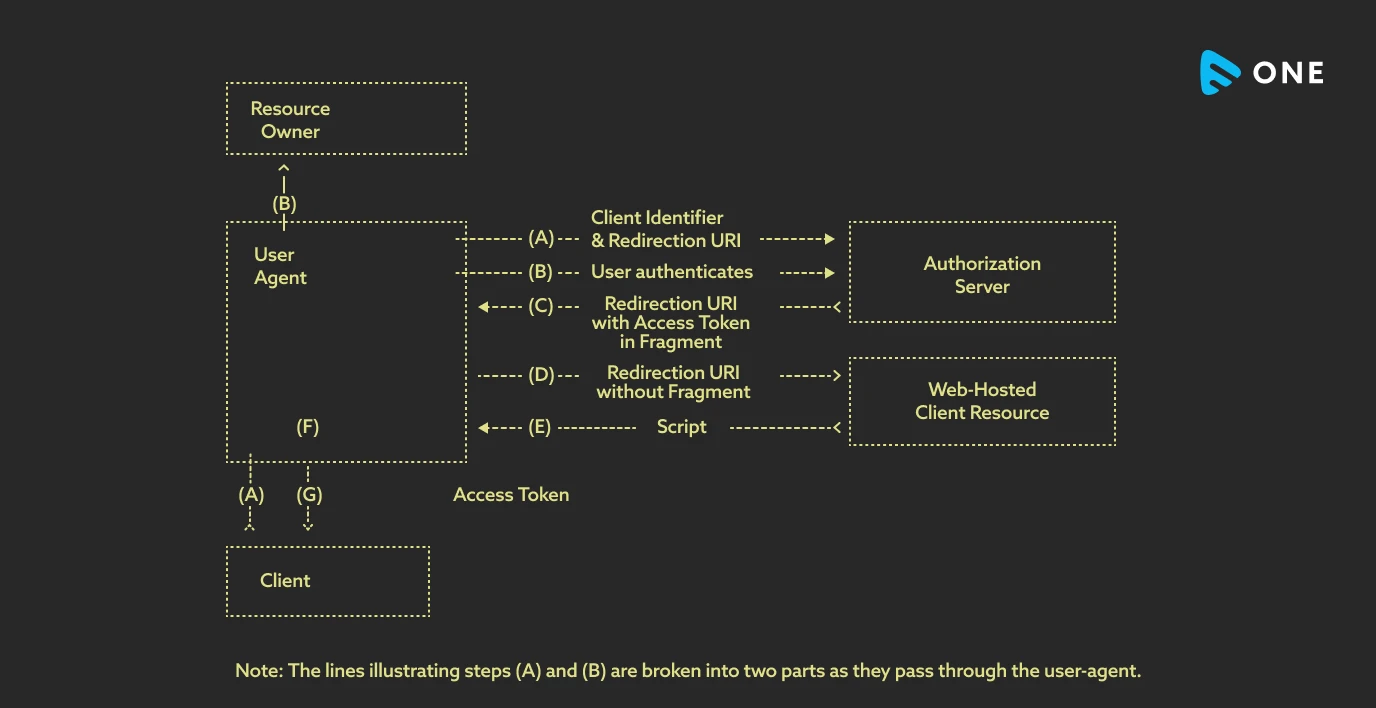
Implicit Grant
It is a simplified authorization code that is optimized for the clients and is implemented using a scripting language in a browser. JavaScript is the most widely used scripting language in this case, but others can be used too.
In this process, the client is issued an access token directly, instead of just an authorization code. This access code is issued after the resource owner’s authorization. While issuing the access token, the authorization server does not authenticate the user. Rather, you need to use the redirection URI that was used to deliver the access token to verify the user.
As you can see, no intermediate authorization credentials are issued in this process. That is why, this process is called implicit.
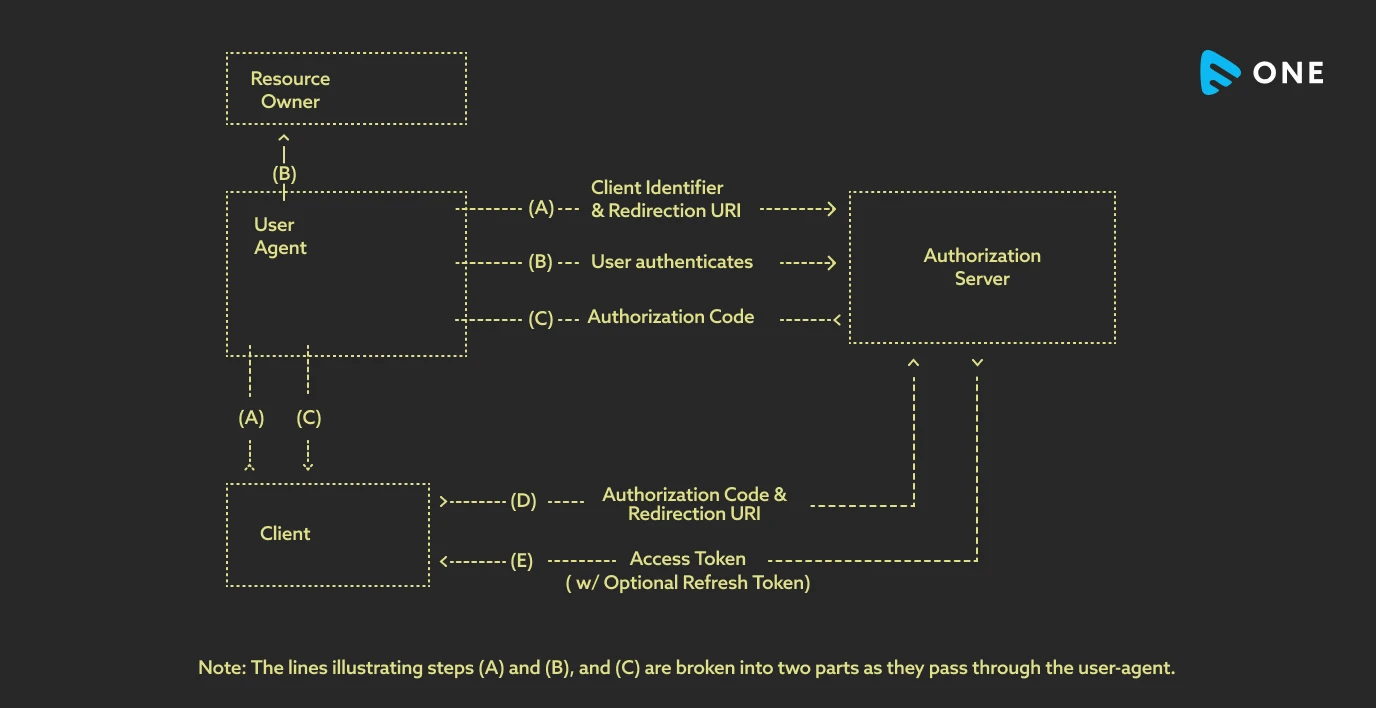
Authorization-code Grant
In this process, an authorization code is issued by the authorization server. In this case, the authorization code acts as a bridge between the user and the admin. The user does not request authorization directly from the admin. Rather, it directs the admin to the authorization server, which then offers the authorization code to the admin, using which the authorization can be done. Before issuing the authorization code, the server first verifies the admin and then issues the code.
Advantages of SSO
Single Sign On have a lot of advantages both for the users and the admins. Let’s take a look at some of them one by one.
Benefits of SSO for the Users
- Users need only one username and password (and literally only one account) to sign on to multiple platforms, applications, and devices. Hence, it saves their time and makes the process easy.
- It becomes easy for them to remember the username and password, as there is only one account for multiple services.
- They get automatically logged in to multiple applications and services and do not have to write down their login credentials on multiple screens.
Benefits of SSO for Admins and Service Providers
- Admins can easily manage the user identities, which is a tiring job in case of multiple logins.
- They can maintain a central point for managing the users, as the same user is not logging in through multiple screens.
- This is a more secure and easily manageable login process. ‘
How Does SSO Help in Security and Access Management?
Single Sign On has a huge role to play in security. And when we say security, we mean overall security, for both the users and the admins.
Since SSO ensures that you have only one password for multiple platforms, the users can afford to have stronger passwords, since they do not need to remember multiple passwords. This also helps in reducing “Password Fatigue”, that might arise due to the same passwords for multiple platforms.
Multi-factor authentication can also be implemented using SSO. It means that the users can use more than one factor for authentication. While one factor is password, the other can be biometric identity like fingerprint, Face Scan, or even iris scan.
For businesses, SSO helps to manage all the user sessions from a central place, hence nullifying the chances of unwanted access. The companies can maintain detailed activity logs of the users that help in tracking suspicious user behaviors.
The Zero-Trust Approach
Now you might ask, is it ethical to track user behavior? Well, the answer to this question should be NO, but in today’s world full of cybercrime incidents, most organizations prefer to follow the “Zero Trust Approach”.
This Zero Trust Approach refers to a situation where the business always prefers to give access to verified users only. Single sign-on plays a big role in this process. This helps businesses to pre-empt any identity theft or false login attempts.
What are Cloud SSO Solutions?
Nowadays, most of the applications and digital services operate from the cloud. Cloud Single Sign On is the process of gaining access to multiple cloud-based applications and services through SSO. Hence, all these cloud-based applications can be accessed via a single set of login IDs and passwords, through a single login session. Cloud SSO is one of the most important cloud security techniques that is crucial for offering a secure experience to users.
Risks Involved With SSO
Just like any other technology has both good and bad, SSO also has both advantages and risks. The benefits of Single Sign On are multiple, as already discussed before. However, SSO has one major risk of password compromise.
Though SSO passwords are by default stronger than normal passwords, the importance of SSO passwords is also much higher. A single password can grant access to multiple applications. Hence, by any chance, if that password gets compromised, the hacker gains access to all the applications.
The Different Variations of SSO
The applications of Single Sign On are quite diverse. And according to its applications, there are different variations of SSO integration. Let’s take a look at some of them.
Adaptive SSO
As its name suggests, this Single Sign On adapts itself to the type of risks involved in the sign-in process. When a new user logs in for the first time, it will ask for only a username and password, and grant access to the user easily.
But if there are suspicious and risky login attempts, like login to the same account from multiple devices, or multiple locations, then the user might have to provide additional credentials, including verification codes and biometrics.
Federated SSO
It is not a full SSO integration, rather it is a superset of SSO. It is also called the FIM (Federated Identity Management). If you already have SSO integrated within your organization, then you can use FIM to extend access to third-party vendors and other accounts that are not directly under your organization but indirectly linked to your business.
Social Log-Ins
We all are quite familiar with this version of SSO integration. In real life, we come across many applications and websites that allow us to log in via our Facebook, LinkedIn, or Google accounts. This is an example of Social login, where the user can use their social media profile to log in to third-party applications.
SSO Glossary
Since SSO is a vast technology, there are multiple technical terms involved in it. To help you understand them better, we have tried to explain some of those terms in this glossary.
Third-Party Application or “Client”: The application that is attempting to gain access to the user’s account is called Client. The user MUST give permission to the client for this process.
Resource Server: The resource server is the API server used to access the user’s information.
Authorization Server: This server presents the interface over which the user approves or denies the request.
Resource Owner: The person who is giving access to their account.
Redirect URIs: These URIs can only redirect users to a registered URI. It helps to prevent certain cyber attacks.
Wrapping Up
In this blog, we try to explain the various technologies and implementation techniques involved in SSO. Nowadays, most of the applications are implementing single sign on due to the multiple security and administrative benefits that it offers.
Even many no-code platforms like Muvi offer SSO as a built-in feature. Whenever you create websites or applications using Muvi One, you can integrate the SSO feature into the apps and website. This helps you manage all your users more easily.
Apart from the SSO, some of the core features of Muvi One include:
- Built-in CDN
- Built-in DRM
- Multiple monetization models
- Geo-blocking
- Both VOD and Live Streaming supported
- Static, dynamic, and forensic watermarking
- Metadata management
- Device management
- HTML5 video player
- Audio player and podcast support
- Mobile and TV Apps for 16+ OS environments
- Performance and audience analytics
Some of the major advantages of using Muvi One for developing your own streaming platform:
- You can develop mobile and TV apps for literally any OS environment within minutes.
- You can customize the design of your entire platform using our visual designer.
- You get a 14-day free trial, without submitting any credit card details.
Our USPs:
- Unlimited features.
- Unlimited Customization.
- Unlimited Support.
So why wait? Start developing your own branded streaming platform using Muvi One today! Sign up to start your 14-day free trial right now.













Add your comment