The number of businesses migrating their data to the cloud has been increasing consistently since cloud platforms provide enterprises with a more secure outlet for storing their content, applications, and data. For businesses making the transition to the cloud, robust cloud security is imperative. With security threats constantly evolving into more sophisticated forms, cloud security is no less at risk than an on-premise ecosystem. For this reason, it is essential to choose a cloud server that offers best-in-class security customized for your infrastructure.
What is Cloud Security?
Cloud security consists of a set of policies, strategies, controls, and practices that work together in unison for protecting data and applications that are hosted in the cloud. These security standards are designed to protect the data in the cloud, support regulatory compliance, safeguard the clients’ privacy as well as setting authentication rules for individual users and devices.
Tailored to suit business requirements, cloud security is a broad area involving a multitude of different security practices right from authenticating user access reviews to filtering traffic. And since the cloud gives the option of configuring and managing all these rules at one centralized location, administration overheads are greatly reduced. The integration of a cloud security assessment tool here plays a critical role in continuously evaluating the effectiveness of these controls and ensuring compliance with security policies.
While comparing cloud computing with on-premise servers, though it often seems that on-premise servers are more secure due to in-house hardware and personalized data stack, it is undeniable that cloud servers provide more security layers than on-premise setup. This is because cloud servers have more resources for keeping data secure than on-premise setup, which ultimately helps in maintaining an upgraded infrastructure removing any kind of vulnerabilities as soon as possible.
What are Some of the Risks of Cloud Security?
Due to its open architecture, online availability, and interconnectedness, a cloud computing environment can become vulnerable to a few security threats:
- Data leakage and data loss
- Unauthorized user access to internal data
- Malicious attacks, such as DDoS attacks or malware infections, that can cripple a cloud infrastructure
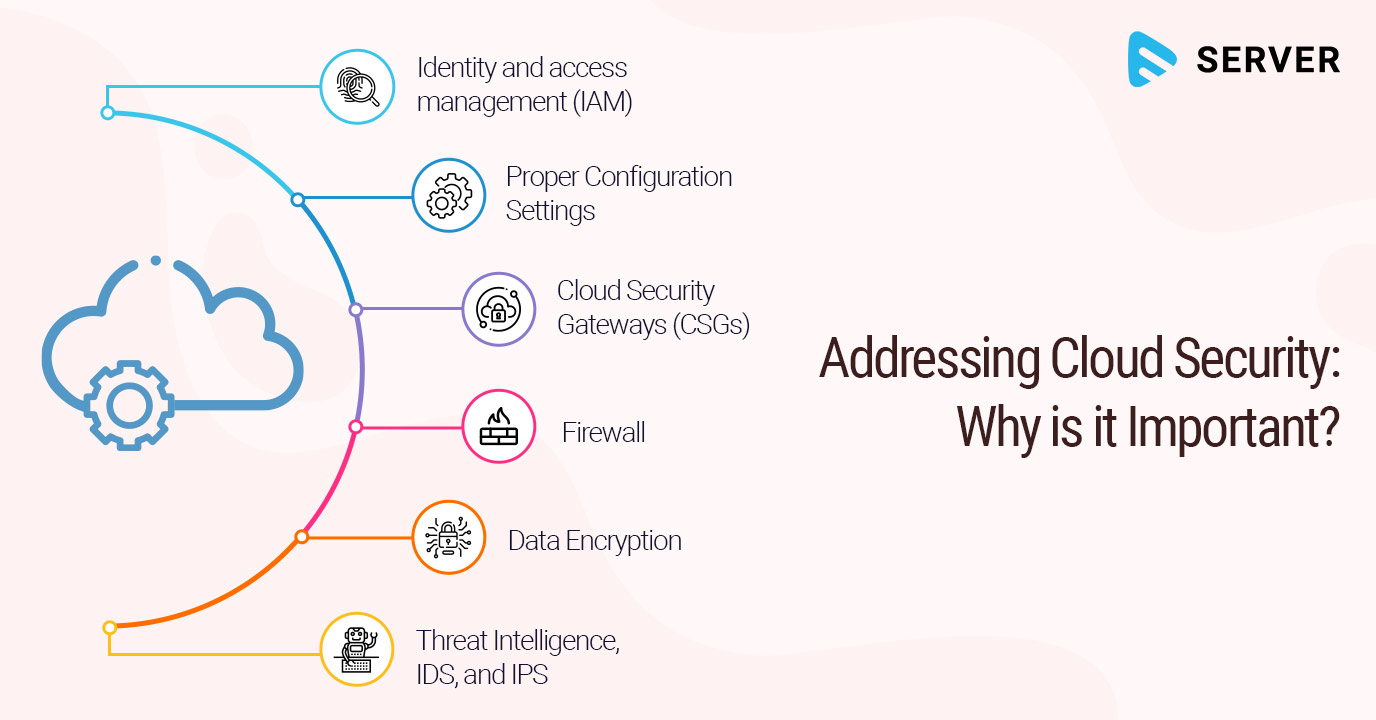
Some Important Practices Enhancing Cloud Security
To prevent organizations from facing the above-mentioned security threats, a best-in-class cloud security strategy should include all of the following technologies:
1. Firewall: A firewall is a security product used by cloud servers that filters out malicious traffic. A cloud firewall blocks cyber attacks directed at cloud assets by providing a protective shield around these assets. In the same way, as traditional firewalls form a barrier around an organization’s internal network, cloud firewalls are hosted in the cloud and form a virtual security barrier around cloud infrastructure protecting traffic going to, from, and between applications in the cloud. Cloud firewalls block DDoS attacks, malicious bot activity, and vulnerability exploits.
Muvi Server takes care of your valuable content by providing advanced security measures like server-side security and firewall, protecting the storage and delivery of high-valued & original content to any device.
2. Data Encryption: Data encryption is the process of encoding data as it travels to and from cloud-based applications and storage to authorized users of that data at their locations. The process involves the deployment of strong key-based encryption encoding/decoding that prevents unauthorized users from intercepting data streams as they travel to and from the cloud, or from accessing data files when they are saved to cloud storage.
So, if an attacker tries to hack into a company’s cloud, the data is already encrypted and it cannot be hacked unless they somehow manage to find the decryption key, the chances of which are highly improbable. In this way, encryption helps prevent data leakage and exposure, even when a few layers of security are breached (which is highly unlikely).
3. Identity and access management (IAM): Identity and access management (IAM) is the process of tracking down a user and allowing only authorized users to access data while denying access to unauthorized ones. IAM is a system that manages a given set of users’ digital identities, and the privileges associated with each identity. IAM is extremely important in cloud computing because a user’s identity and access privileges determine whether they can access data or not. In addition, privileged access management (PAM) is often used alongside IAM to provide additional control over users with elevated privileges, ensuring sensitive data and systems remain secure.
An umbrella term encompassing a lot of different services, IAM consists of the following capabilities:
- Multi-factor authentication (MFA) services that reinforce the user authentication process
- Identity providers (IdP) authenticating user identity
- Single sign-on (SSO) services that help authenticate the identity of the user gaining access from multiple applications so that users only have to sign in once to access all their cloud services.
4. Proper Configuration Settings: A cloud server that does not set up their security settings properly can lead to data breaches and can expose data directly to the Internet. Configuring cloud security settings requires team members who are experts in working with each cloud.
5. Cloud Security Gateways (CSGs): CSGs are on-premises or cloud-hosted security software that act as policy enforcement points between a company and cloud applications that employees use. Cloud security gateways consolidate multiple security policies including authorization, authentication, single sign-on, encryption, security token mapping, tokenization, logging, alerting, API control, and so on.
6. Threat Intelligence, IDS, and IPS: Threat Intelligence, Intrusion Detection Systems or IDS, and Intrusion Prevention Systems, also known as IPS, and Cloud Threat Hunting form the backbone of cloud security. Threat Intelligence and IDS are software applications that help detect malicious activity or policy violations, identifying attackers who try to target systems. Intrusion Prevention Systems or IPS is a form of network security that works to detect and prevent identified threats while continuously monitoring your network, looking for possible malicious incidents, and alerting you to its occurrence for immediate response.
To Wrap Up,
It’s imperative to carefully select the right cloud server offering an advanced security solution for your business if you want to get the best from the cloud and ensure protection from unauthorized access, DDOS attacks, data breaches, and other threats.
Muvi Server acts as a unified control plane for security across all types of cloud infrastructure, including hybrid cloud environments. Whether your audio/video content is for public-facing audiences or internal communications, Muvi Server safeguards your content from unauthorized access and tampering. To host and manage your videos and audios securely and reliably, take a 14-Day Free Trial, now!







Add your comment